There are different types of VPN. If you are not aware of them yet, you should complete reading this article. You might have used a VPN service at least once in your life. They are very useful in several situations. But what about the VPN types? What actually has to do with the VPN service and reliability? This article will solve all your questions regarding the VPN types.
What are VPN Types?
VPN types are generally based on their connection type and the security they are providing. Mostly based on the connection type. There are several types of VPN connections discovered to date. They include the most commonly used PPTP type to the rarest Hybrid type. Based on the requirement of the user, the type of VPN also changes. For example, for a person who just needs basic connection security doesn’t need a much costly and effective VPN like an enterprise with highly confidential data. To know more about the VPN types, read the below list.
1. PPTP VPN
PPTP of Point-to-Point Tunneling Protocol is the most common and popular VPN type out there. If you are going to buy a simple VPN without doing much research about its type, you are probably going to get a PPTP VPN. The PPTP VPNs create a tunnel different from internet service providers and capture the data. This allows users to browse anonymously on the internet and protect their network with strong encryption standards. Users will be given the credentials including an approved password in order to start using the VPN service. Users will have to enter these details while setting up the VPN.
PPTP VPNs are compatible with almost all operating systems including Windows, Mac, and Linux. This is also a reason for the popularity and widespread usage of the Point-to-Point VPN networks. If you are a beginner and just need a simple VPN service that is strong enough to secure your connection, you should go with a PPTP VPN.
Takeaways
- Common and popular VPN type
- Creates a tunnel for anonymous browsing
- Compatible with various operating systems
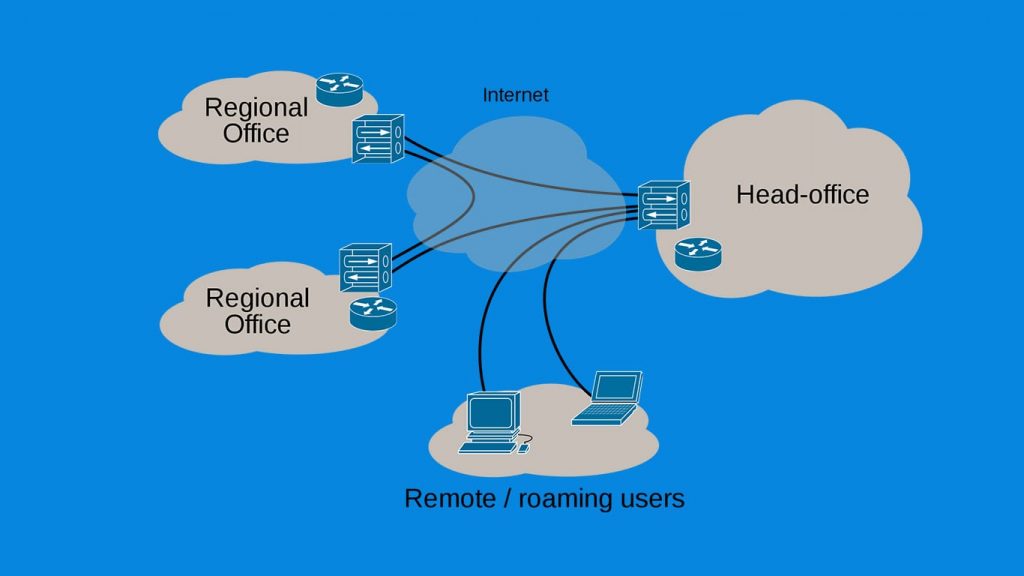
2. Site-to-Site VPN
Site-to-Site or Root-to-Root VPN also known as the Intranet-based VPN is mostly used by companies that have offices both locally and internationally. The companies use such VPN connections to interconnect their offices to the main branch. Companies also use the Site-to-Site VPN to connect with other companies which are known as the Extranet-based VPN. Like the PPTP VPNs, the connections will be highly secure or even better in this type of VPNs.
Takeaways
- Used by companies with local and international offices
- Connects offices to the main branch or other companies
- Provides highly secure connections
3. L2TP VPN
L2TP or Layer to Tunneling Protocol is a type of VPN that combines with other VPN protocols to result in a VPN with better security. To be more precise, the L2TP VPN forms a tunnel between two L2TP connections, and then another VPN is applied to secure the communication through the L2TP tunnels. It is developed by the tech giants Microsoft and Cisco.
Takeaways
- Combines with other VPN protocols for better security
- Forms tunnels between L2TP connections
- Developed by Microsoft and Cisco
4. SSL and TLS
SSL (Secure Socket Layer) and TLS (Transport Layer Security) type make the browser to serve as the client and user access is restricted to specific applications only. This will restrict access to the specific user instead of an entire network. We all see the HTTPS before some shopping websites and eCommerce sites. They are secured by the SSL encryption.
Takeaways
- Uses browser as the client
- Restricts access to specific applications or users
- Provides secure encryption (e.g., HTTPS)
5. IPsec
IPsec or Internet Protocol Security is used to secure communication across an IP network. In such a VPN, a tunnel is set up in a remote site that allows access to your central site. The IPsec works by verifying each and every session and individually encrypts the data packets throughout the network. The IPsec can be used as an addition to other VPN types to enhance the security of the connection.
There are two modes of IPsec which are the transport mode and tunneling mode. In transport mode, the message in the data packet is encrypted while in the tunneling mode, the entire data packet is encrypted.
Takeaways
- Secures communication across IP networks
- Verifies each session and encrypts data packets
- Offers transport mode and tunneling mode
6. MPLS VPN
MPLS or Multi-Protocol Label Switching is used to speed up the distribution of network packets over multiple protocols. It is one of the most flexible VPN types out there. So, it is widely used for the Site-to-Site type of connections. MLPS are basically ISP tuned which means two or more sites are connected to form a VPN using the same Internet Service Provider. It is very difficult to set up and configure an MPLS VPN and very costly too. So, it is not recommended for people who don’t know about it much.
Takeaways
- Speeds up network packet distribution
- Suitable for Site-to-Site connections
- Requires expertise to set up and configure
7. Hybrid VPN
Hybrid VPN is a combination of the MPLS and IPsec VPN. Usually, in Hybrid VPN, the MPLS will be used at a certain site and the IPsec on the other. However, it is also possible to use them at the same site.
Like we already discussed, the IPsec requires some equipment on the customer side (like Routers). Through devices like routers, the data is encrypted and transferred through the secure tunnel generated. And the MPLS VPNs require some equipment from the carrier side. To combine both of these, a gateway which eliminates the IPsec tunnel is established and charts it to the MPLS VPN. The security is not affected by this process and the user data will stay encrypted throughout the process.
Takeaways
- Combination of MPLS and IPsec VPN
- Can use both at the same site or different sites
- Maintains security while encrypting data
8. Remote Access VPN
Based on its architecture, the service can be a Remote Access VPN if it has external users on an internal network that exists behind a VPN Gateway or Server. In such cases, the external users are reliant on software, known as VPN Clients, to connect to the VPN network via the Gateway or Server. It is also known as Client-to-Site VPN or Client based VPN. The service is optimal for those who want to access the internet remotely (hence the name). Users of a Remote Access VPN can connect to the network from anywhere, as long they have the relevant VPN Client.
Takeaways
- Allows external users to connect to internal network via VPN gateway
- Relies on VPN clients for connection
- Enables remote internet access securely
9. Host-to-Host VPN
Host-to-Host VPNs work somewhat identically to a Remote Access VPN. However, the difference lies in what the user connects to when using the VPN client. Unlike Remote Access VPN, the user directly connects to a server that is already running a VPN. Hence, Host-to-Host VPNs offer a direct connection to a VPN service on the other endpoint. These VPNs are mostly used when an admin needs secure access to a sensitive server. By running the Host-to-Host VPN, one can easily limit the server access and lock it down to only allow authorized parties.
Takeaways
- Provides direct connection to a server running a VPN
- Ideal for secure access to sensitive servers
- Limits access to authorized parties
So, these are the most important VPN types you should be aware of.
Quick Comparison Table of Different VPN Types
| VPN Type | Description |
|---|---|
| PPTP VPN | Common VPN type for anonymous browsing and multi-platform compatibility. |
| Site-to-Site VPN | Connects company offices securely, including international branches. |
| L2TP VPN | Enhances security by combining with other protocols and forming tunnels. |
| SSL and TLS | Restricts access to specific applications or users using SSL and TLS encryption. |
| IPsec | Secures communication across IP networks with session verification and data encryption. |
| MPLS VPN | Speeds up network packet distribution, ideal for Site-to-Site connections. |
| Hybrid VPN | Combines MPLS and IPsec VPN for enhanced security and encrypted data transfer. |
| Remote Access VPN | Enables secure external access to an internal network for remote internet connectivity. |
| Host-to-Host VPN | Establishes direct, secure connections to sensitive servers for authorized parties. |
Which VPN Type Should I Choose?
It is completely based on your requirements. You should evaluate your requirements with a VPN or what a VPN should do for you. For example, for a person who wants to secure his home internet connection will not need high-end encryption. Like that, for an enterprise with multiple branches all over the world will need a highly secure and encrypted virtual private network to stay safe.
So, do research about the available VPN services and compare their features as well as the pricing. Go for the best VPN service which provides the best features for an affordable rate. You could also go for a free VPN service if you don’t have any budget to spend on the VPN.
